Rumored Buzz on S3 Backup
Wiki Article
The Main Principles Of Aws Cloud Backup
Table of ContentsFascination About Aws S3 BackupNot known Factual Statements About Rto Not known Details About Protection Against Ransomware The Ultimate Guide To Aws Cloud Backup
utilities that enable you to keep track of as well as filter network web traffic. You can use firewall programs to guarantee that only authorized users are permitted to accessibility or transfer information. controls that assist you validate qualifications and assure that customer privileges are used properly. These steps are generally used as part of an identification and also accessibility administration (IAM) service and in combination with role-based gain access to controls (RBAC).Security safeguards your data from unapproved gain access to also if data is taken by making it unreadable. Endpoint protection software application generally enables you to monitor your network border and to filter web traffic as required.
This can be done after information is refined and also examined or occasionally when information is no much longer relevant. Erasing unnecessary data is a requirement of numerous compliance guidelines, such as GDPR.

All about Ec2 Backup
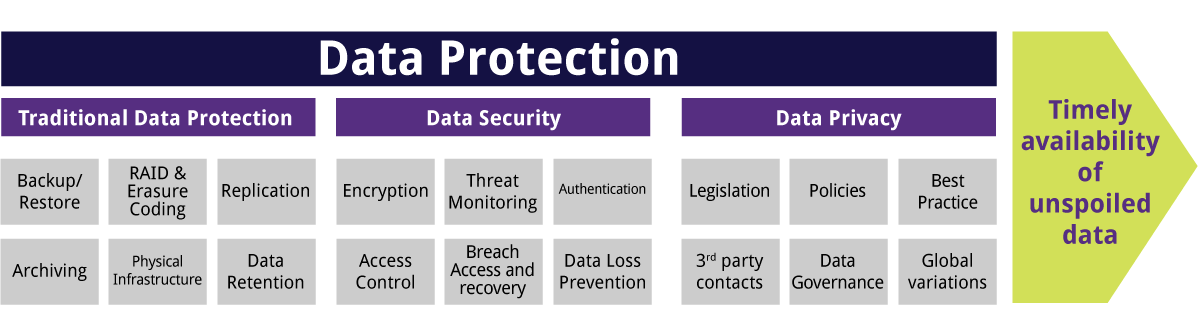
Reducing your information collection can likewise help you save on transmission capacity as well as storage. These systems use third-party information to confirm customers and remove the need to shop or transfer customer information to your systems - https://clumi0.start.page/.
Mirroring this, GDPR has made individual consent a crucial facet of data use as well as collection. You can be certain to include individuals and also their approval in your processes by making privacy worries right into your interfaces. data protection. Having clear user notifications describing when information is accumulated and also why. You need to also include choices for customers to modify or opt-out of data collection.
Information portability is an important demand for numerous modern-day IT companies. It suggests the capacity to move data between different environments and software applications. Really often, data portability means the capacity to relocate data between on-premises information facilities as well as the general public cloud, as well as in between different cloud suppliers. Data portability also has legal implicationswhen data is saved in different nations, it undergoes various legislations and regulations.
Our Aws S3 Backup Statements

This makes it tough to relocate data from one cloud to an additional, and also creates supplier secure. Significantly, companies are searching for standardized methods of keeping as well as taking care of data, to make it mobile throughout clouds. Mobile device protection refers to steps created to secure delicate info saved on laptop computers, smart devices, tablet computers, wearables and also various other mobile tools.
In the modern-day IT setting, this is a critical facet of network security. There are many mobile information protection devices, created to shield mobile phones as well as information by recognizing hazards, developing backups, as well as avoiding risks on the endpoint from getting to the company network. IT personnel use mobile data security software program to allow safe and secure mobile accessibility to networks as well as systems.
Ransomware is a sort of malware that secures individual data and requires a ransom in order to release it. Brand-new types of ransomware send out the information to enemies prior to securing it, enabling the assailants to obtain the company, endangering to make its delicate info public. have a peek at this site Back-ups are a reliable defense versus ransomwareif an organization has a current copy of its information, it can restore it and reclaim access to the information.
The Single Strategy To Use For Rto
At this phase ransomware can contaminate any kind of connected system, including back-ups. s3 cloud backup. When ransomware infects back-ups, it is "game over" for information protection approaches, because it ends up being difficult to recover the encrypted data. There are several methods for preventing ransomware as well as particularly, avoiding it from spreading to backups: The easiest method is to utilize the old 3-2-1 backup policy, keeping three copies of the data on two storage space media, one of which is off premises.Storage space vendors are using immutable storage space, which ensures that information can not be modified after it is kept (https://codepen.io/clumi0/pen/ExRggQj). Huge companies have actually multiple datasets kept in various places, as well as numerous of them may replicate information between them.
It is no usage safeguarding a dataset and guaranteeing it is certified, when the data is duplicated in one more unidentified area. CDM is a sort of option that detects duplicate information and also aids handle it, comparing similar data as well as allowing administrators to erase extra duplicates. Disaster recuperation as a solution (DRaa, S) is a managed service that offers a company a cloud-based remote disaster recovery site.
With DRaa, S, any type of dimension company can reproduce its neighborhood systems to the cloud, and also easily restore operations in situation of a catastrophe. DRaa, S services take advantage of public cloud facilities, making it feasible to keep several duplicates of facilities and also information across several geographical places, to boost resiliency. Information defense needs powerful storage innovation (https://www.pinterest.com/pin/907475393641930133/sent/?invite_code=04e56aa744e14394b363733bb3859de0&sender=907475531073705692&sfo=1).
Report this wiki page